Half of Irish companies have been victims of economic crime within the past two years — up from 34pc in 2016 and 26pc in 2010, according to a recent report from PwC on economic crime (stock image) Brand damage and embarrassment are among the reasons given for the under-reporting of cybercrime by Irish businesses to gardai. But, from a prevention and awareness level, it is important that this crime is reported, according to Michael Gubbins, Detective Superintendent and head of the Garda National Cyber Crime Bureau. It is estimated that…
Read MoreTag: cyber crime
New Intel security flaw allows remote access to corporate laptops by hackers
Remember the latest “Spectre” and “Meltdown” vulnerabilities recently found in the micro-chips that are used in almost all computers, tablets and smartphones today? A new security flaw has been found in Intel hardware by Finish company F-Secure. The new vulnerability could enable hackers to access corporate laptops remotely. F-Secure said in a statement that the flaw was an issue within Intel Active Management Technology (AMT), “which is commonly found in most corporate laptops, (and) allows an attacker to take complete control over a user’s device in a matter of seconds,”…
Read MoreHackers Threaten ‘Game of Thrones,’ as HBO Confirms Cyberattack
HBO has been the latest target of a cyber-attack. HBO confirmed on Monday that the network had been the target of a cyberattack, as an anonymous hacker boasted about leaking full episodes of upcoming shows along with written material from next week’s episode of “Game of Thrones.” The hack was announced to media via an anonymous email which claimed 1.5 terabytes of data from secure HBO networks was accessed, according to Entertainment Weekly. Unaired episodes of “Ballers” and “Room 104” may have been published online, and the hacker vowed more…
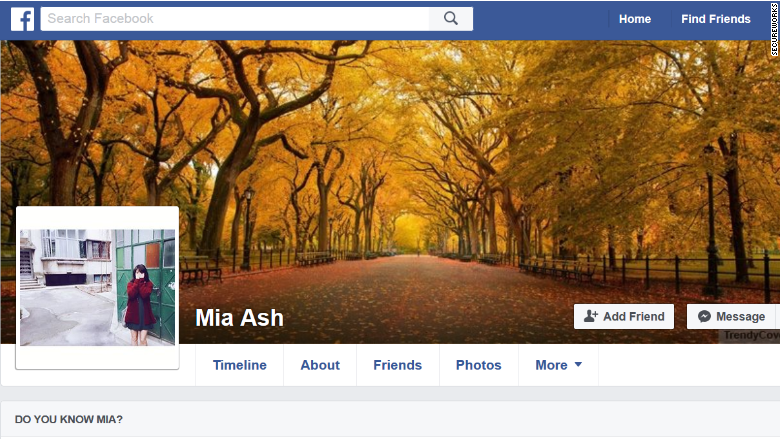
Read MoreCyber spies use female ‘honey pot’ to lure LinkedIn targets
MIA Ash is an attractive 30-year-old British woman with two art school degrees , a successful career as a photographer with hundreds of social media connections. She has common favorite hobbies with social media users, so when she adds a target as a friend, they probably get flattered and a little bit excited. After exchanging messages on LinkedIn, The target is happy to continue the conversation on Facebook and WhatsApp. One problem though, Mia does not exist. Instead, she’s a persona, her biography fabricated and her photos stolen from another…
Read MoreMicrosoft Patches 56 Vulnerabilities
Microsoft has released an urgent update to stop hackers taking control of computers with a single email. The unusual bug, in Microsoft anti-malware software such as Windows Defender, could be exploited without the recipient even opening the message. Researchers working for Google’s Project Zero cyber-security outfit discovered the flaw at the weekend. The fix has been specially pushed out hours before the software giant’s monthly Tuesday security update. The update CVE-2017-0290 addresses a vulnerability that could allow remote code execution if the Microsoft Malware Protection Engine scans a specially crafted file.…
Read MoreGoogle’s battle with Android malware: Who wins?
While most people are aware of the malicious threats targeting their computers, many still don’t realise that their mobile devices are an increasingly lucrative a target for cybercriminals. The main way smartphones are attacked is though apps, often ones which pose as innocent and useful but actually aim to steal data or in the case of ransomware, force users to pay up. Recently, google uncovered the Android version of Pegasus, a mobile spyware created by NSO Group, an Israeli surveillance company considered the most advanced producer of mobile spyware on…
Read MoreGoogle Docs phishing attack is fixed
Google Docs users were hit by a widespread phishing attempt everywhere being spammed with what appeared to be malicious invitations to log on to their Google accounts. Unlike your garden-variety cyberattack, many of the telltale signs that could tip off that something was awry are absent. What made this attack so tricky to detect was that it took advantage of Google’s legitimate tool for sharing data with responsible third-party apps. Since the bogus invitation was being routed through Google’s real system, nothing was misspelled, the icons looked accurate, and it’s hard to know something’s…
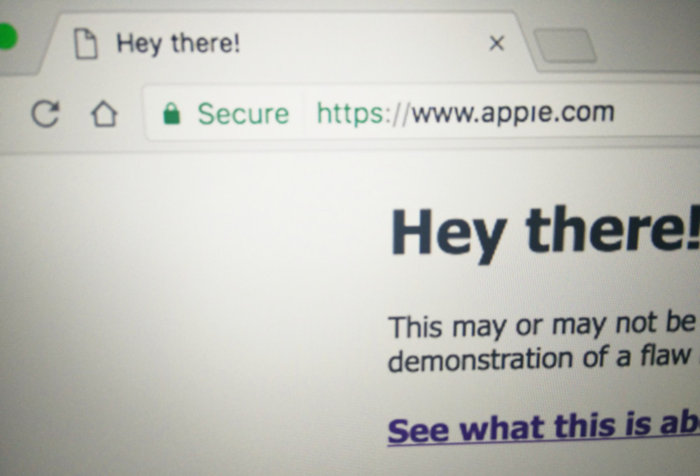
Read MorePhishing attacks using internationalized domains are hard to block
Attackers can evade a security mechanism and abuse Unicode domains to phish for the login credentials of Chrome, Firefox, and Opera users. Security researcher Xudong Zheng has developed a proof-of-concept that exploits an issue in some web browsers. Attackers can abuse this sleight of hand to redirect users to phishing websites. All they need to do is use Punycode, which relies on ASCII characters to convey foreign characters. The Punycode domain “xn--pple-43d.com” is equivalent to “apple.com”, for example. As long as a web browser translates the Punycode into what’s known…
Read MoreArtificial intelligence could be the key to cyber security
In a constantly evolving digital threat landscape, where firewalls and antiviruses are considered tools of antiquity, companies are looking to more technologically advanced means of protecting crucial data. Experts point out the cyber-threat landscape has drastically changed and that criminals are now using more artificial intelligence technologies to launch sophisticated attacks. Even a few years ago, launching a distributed denial of service attack to take down a website, defacing webpages and stealing credit card details were considered major instances of cyber-attacks. Today, anything from medical records to airline miles data…
Read MoreCyber crime is fastest growing economic crime
Cyber crime is perceived as the fastest growing fraud risk (40%), followed by bribery and corruption (36%)around the globe. The UK has seen a double-digit rise in economic crime against corporates in the past two years, with 55% of organisations affected up 11% since 2014 and well above the US (38%) and China (28%). Globally, the economic crime rate has remained largely static at 36%, according to the survey of more than 6,000 respondents in 115 countries. The survey found that 60 % of economic crime in the UK was…
Read More