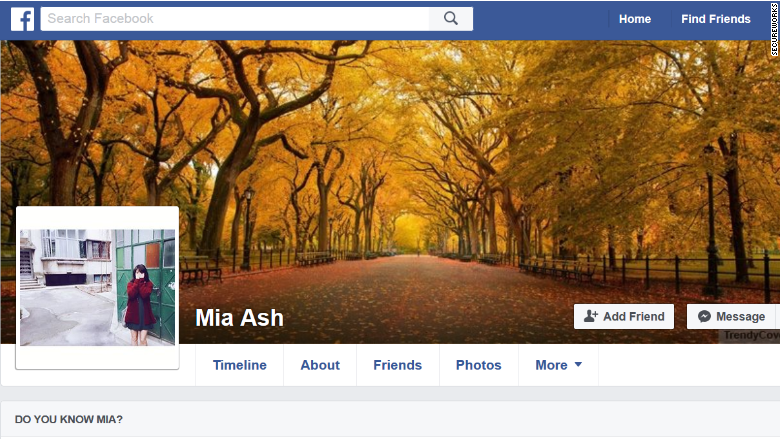
MIA Ash is an attractive 30-year-old British woman with two art school degrees , a successful career as a photographer with hundreds of social media connections.
She has common favorite hobbies with social media users, so when she adds a target as a friend, they probably get flattered and a little bit excited. After exchanging messages on LinkedIn, The target is happy to continue the conversation on Facebook and WhatsApp. One problem though, Mia does not exist.
Instead, she’s a persona, her biography fabricated and her photos stolen from another woman’s online profiles, according to researchers at the security firm SecureWorks. The research reports that a hacking group linked to Iran is believed to be behind Mia Ash personality.
Online “honey pot” attackers like Mia Ash represent a new front in a global espionage, with hackers targeting strategically important companies through their weakest line of defence: their hapless employees.
SecureWorks calls the hacking group Cobalt Gypsy, also known as OilRig by other researchers. The group has previously targeted Saudi Arabian oil, financial and tech executives, as well as Israeli corporate networks.
The intent was to steal credentials from employees who would have access to their companies’ computer networks. For example, the fake account sent a phishing email to one of the men she befriended containing malware. This would give the hackers control of his computer, SecureWorks found.
According to Allison Wikoff, the lead researcher on the investigation into Cobalt Gypsy, LinkedIn can be a successful way for hackers to target people because users are inclined to trust others on the site. The hackers who posed as Mia used LinkedIn before switching to more personal communications channels like WhatsApp and Facebook.
According to Wired, SecureWorks also identified the real-life woman whose photos hackers used to assemble Mia Ash’s profiles. But when WIRED reached out to her she declined to speak on the record, and asked not to be identified.
Wikoff points to her case as an example of how publicly posting personal photos can have unexpected, creepy consequences. “If you don’t lock down your social media accounts, they can be used in ways that might not directly harm you, but are nonetheless nefarious,” Wikoff says.
But Mia Ash offers a more serious lesson to possible victims of state-sponsored hackers, Wikoff says: Digital honey traps can be highly sophisticated, with personas that appear to have long histories and convincing personalities. And that attractive new Facebook friend may not actually be into your vacation photos.