Are you inactive on Twitter and still plan on being on the app? Then you better watch out and keep an eye on your account because Twitter plans on deleting the inactive accounts. Consider being active in order to save your account. Earlier last week, Twitter said that it would in this coming month begin removing inactive accounts from their platform. But the company then walked back on that promise because of an uproar, particularly from those who had deceased relatives with inactive accounts and wanted to have some way…
Read MoreTag: Security
Microsoft to offer paid Windows 7 Extended Security Updates after January 14, 2020
Microsoft said last Fall that it would offer paid Windows 7 Extended Security Updates on a per-device basis for big customers willing to pay for them after the company ends Windows 7 support on January 14, 2020. Microsoft officials wouldn’t talk about how much those updates would cost, beyond saying they’d get more expensive over time. Windows 7 Extended Security Updates for three years, meaning through January 2023. These will be security patches/fixes like the ones Microsoft is currently providing for free for Windows 7 users, as Windows 7 is still in “Extended”…
Read MoreNew Intel security flaw allows remote access to corporate laptops by hackers
Remember the latest “Spectre” and “Meltdown” vulnerabilities recently found in the micro-chips that are used in almost all computers, tablets and smartphones today? A new security flaw has been found in Intel hardware by Finish company F-Secure. The new vulnerability could enable hackers to access corporate laptops remotely. F-Secure said in a statement that the flaw was an issue within Intel Active Management Technology (AMT), “which is commonly found in most corporate laptops, (and) allows an attacker to take complete control over a user’s device in a matter of seconds,”…
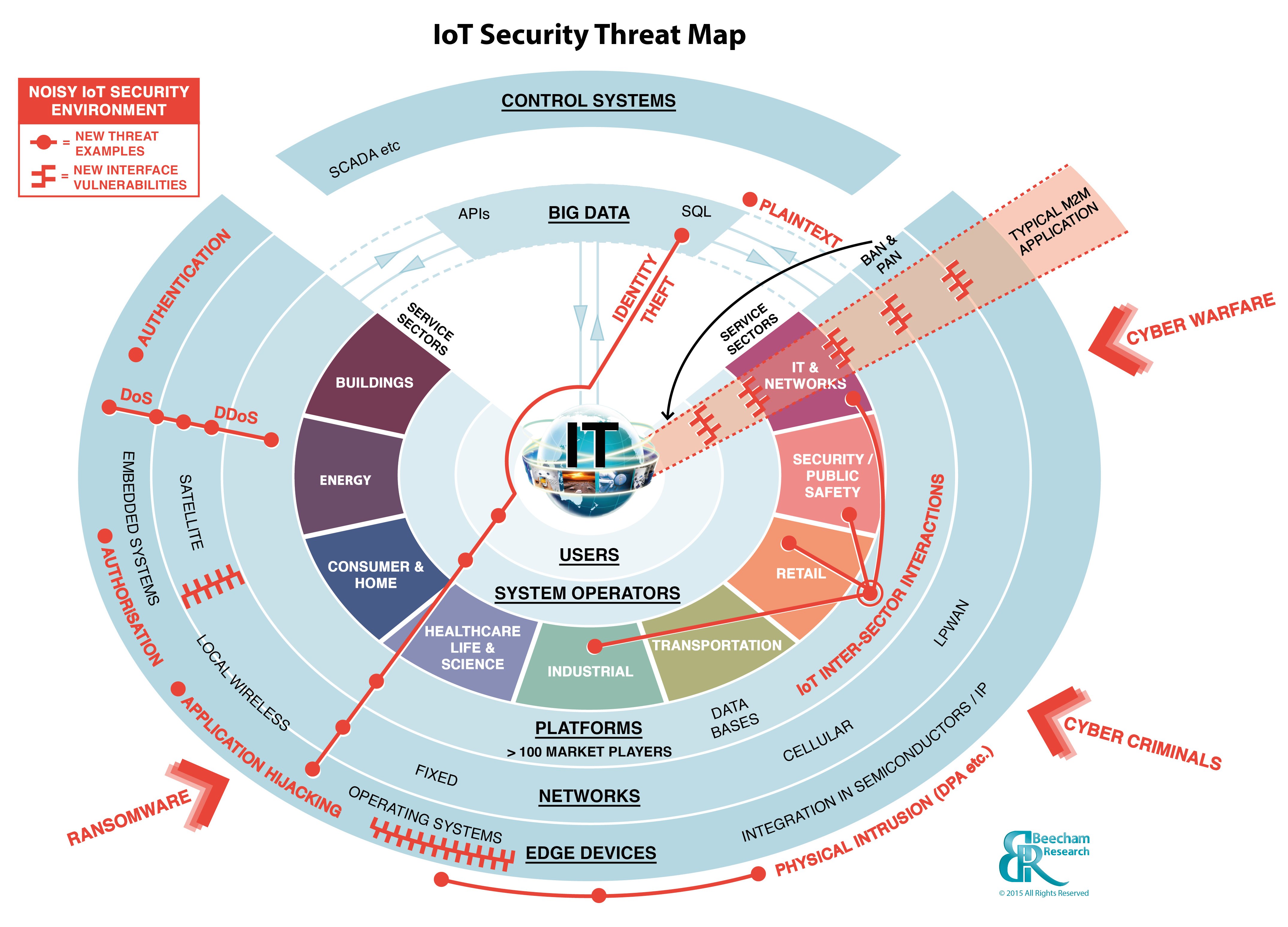
Read MoreInternet providers could easily snoop on your smart home
IoT devices often identify themselves voluntarily, usually by connecting to specific domains or URLs. Even if they didn’t, there are simple ways of profiling them based on observation and some known data. It’s certainly true that encryption is on the rise online. Data from Mozilla, the company behind the popular Firefox browser, shows that more than half of web pages use HTTPS, the standard way of encrypting web traffic. When sites like The Atlantic use HTTPS, a lock icon appears in users’ web browsers, indicating that the information being sent…
Read MoreExplore the latest threats to your mobile device security
It is common knowledge that mobile devices are integral to both our personal and business lives. With cyberattacks against individuals, businesses, and government entities increasing in frequency and sophistication, it is no surprise that mobile devices are now considered by threat actors to be one of the weakest links in the IT infrastructure of most enterprises. A decade ago, mobile malware was considered a new and unlikely threat. Many mobile device users even considered themselves immune from such threats. Currently, more than 1.5 million new incidents of mobile malware have…
Read MoreLinkedIn loses legal right to block startup from public profile data
A Judge on Monday ruled that an analytics company has the right to scrape data from LinkedIn . HiQ, the data gatherer, has been processing publicly available data from LinkedIn and using it to train AI models, until May when LinkedIn demanded it stop. U.S. District Judge Edward Chen in San Francisco granted a preliminary injunction request brought by hiQ Labs, and ordered LinkedIn to remove within 24 hours any technology preventing hiQ from accessing public profiles in a test of how much control a social media site can wield…
Read MoreAmid cyberattacks, ISPs try to clean up the internet
Antivirus software is not what it used to be. The sneaky, sophisticated security threats your PC faces now have gone far beyond what traditional software can do. The future of protecting your PC will require a multi-pronged approach involving vigilant updates, bug bounties, and artificial intelligence. If your computer’s been hacked, Dale Drew might actually know something about that. Dale Drew, the chief security officer at a major internet backbone provider that’s routinely on the lookout for cyberattacks on the network level has led the company to linked more than…
Read MoreNew York unveils final cybersecurity regulations
Cybercriminals can cause significant financial losses for business entities as well as for consumers whose private information may be revealed and/or stolen for illicit purposes. The financial services industry is a significant target of cybersecurity threats. The New York Department of Financial Services unveiled the final cybersecurity regulations, which includes certain regulatory minimum standards while encouraging firms to keep pace with technological advances. New York is the financial capital of the world, and it’s critical that we do everything in our power to protect consumers and our financial system from the…
Read MoreThe Internet of Things has Inspired a New Startup Niche
The Internet of Things has hugely expanded the number of home security products on the market reports The Entrepreneur. Computers were pretty much the only devices that connected to the internet some years back. These days, that idea is a fairytale. The reality is an incredible number of products are now connected to the web, from refrigerators to watches, clothing, cars, thermostats, light bulbs, and alarm systems. By 2020, an estimated 20-plus billion items will belong to the so-called “Internet of Things” (IoT). The Internet of Things has made possible unprecedented innovations in home…
Read MoreInternet of Things based DDoS attacks to rise in 2017
Cyber criminal networks are increasingly taking advantage of the Internet of Things era to spread malware and create zombie networks, or botnets, unbeknownst to their device owners. According to the Indian express the cyber-criminals will use the distributed denial of service (DDoS) attacks in 2017 to extend their reach as there are now several Internet of Things (IoT) devices containing outdated codes and operating with well-known vulnerabilities as reported by a global security firm. The writer says that the criminals will use ever more sophisticated and convincing targeted attacks to lure…
Read More