Twitter is making a play to dominate even more of your time by streaming live video around the clock. The social networking platform is hoping to land deals for streaming pay TV channels on its site and apps. Users have to subscribe to existing TV service for this to work, but it would be much more powerful. “We will definitely have 24 hours a day content on the platform,” Twitter’s Anthony Noto said during an extensive interview about the company’s live video strategy last week. “Our goal is to be…
Read MoreAuthor: Staff Writer
Apple looking to put broadband-beaming satellites into orbit
Apple Inc. is testing self-driving cars and exploring augmented reality. Recent hires suggest the company is now also looking to the skies. The tech giant is getting involved in launching satellites that would beam down broadband Internet access. Recently, Apple poached two Google satellite executives to form a new hardware team within the company. John Fenwick led Google’s spacecraft operations and Michael Trela was head of satellite engineering. Google on the other hand has tempered its own broadband plans as of late. In 2015, the company was simultaneously laying high-speed fiber…
Read MoreGoogle to limit offensive & inaccurate search results
Google is looking forward to impementing changes to its Search Quality Ratings Guidelines in an effort to limit offensive and inaccurate results on its search engine. The tech giant has recently updated its Search Quality Rater Guidelines, which human evaluators use to gauge the quality of search results. The updated guidelines provide clearer examples of low-quality results, including “misleading information, unexpected offensive results, hoaxes and unsupported conspiracy theories,” engineering VP Ben Gomes wrote in the blog post. Google has also tweaked its algorithms to prioritize authoritative results. Human evaluators use…
Read MorePhishing attacks using internationalized domains are hard to block
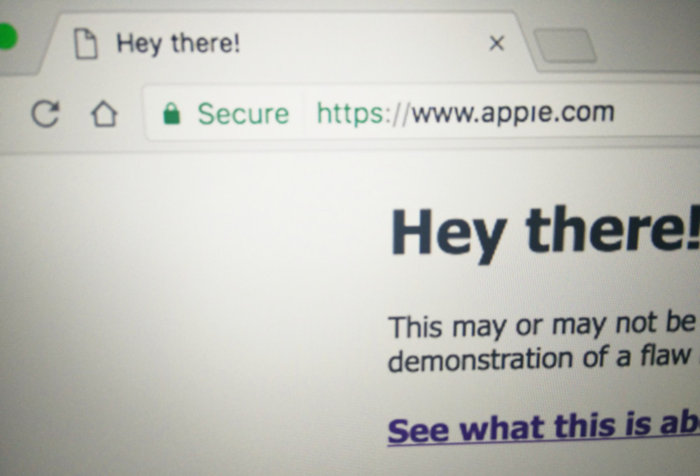
Attackers can evade a security mechanism and abuse Unicode domains to phish for the login credentials of Chrome, Firefox, and Opera users. Security researcher Xudong Zheng has developed a proof-of-concept that exploits an issue in some web browsers. Attackers can abuse this sleight of hand to redirect users to phishing websites. All they need to do is use Punycode, which relies on ASCII characters to convey foreign characters. The Punycode domain “xn--pple-43d.com” is equivalent to “apple.com”, for example. As long as a web browser translates the Punycode into what’s known…
Read MoreNew Screen Protectors For Samsung Galaxy S8 Launched
Tech Armor, the leading screen protector and mobile accessory brand, today launched a new screen protection line for the newly released Samsung Galaxy S8 and Galaxy S8 Plus. With its curved edges, the 3D Curved Ballistic Glass Screen Protector for Samsung Galaxy S8 perfectly matches the rounded shape of the Galaxy S8 to cover the full front display for complete edge-to-edge coverage. The Tech Armor HD FlexiClear Film Screen Protector for Samsung Galaxy S8, a more cost-effective solution, offers edge-to-edge protection as well as flexible shock absorption. To align with…
Read MoreOnly 4% of Uber drivers remain on the platform a year later
Uber’s accelerating driver drop off rate is partially due to increased competition from companies like Lyft. But the number one complaint among Uber drivers is the pay, according to undisclosed data seen by The Information. Many Uber drivers have complained about unfair compensation for long trips, and not being able to accept tips. A spokesman’s reports that they recognize we need to improve our relationship with drivers and their experience using Uber. The ride hailing firm firm is working on a range of improvements across our products, our policies, our customer support and…
Read MoreGoogle to refresh play store
Google has recently started testing a Google Play Store “Refresh” button which allows users to manually check for updates for their Android apps. The button is a part of a larger set of experimental changes that the Mountain View-based tech giant is currently testing and is only available to select users. Provided that the company greenlights the change, the Refresh button will likely roll out to users worldwide in a few months, presumably during the second quarter of the year. The video and screenshots showcasing the latest experimental version of…
Read MoreInstagram on Android gets offline mode
Instagram has announced that android users can now be able to use the photo-sharing app offline. Much of this functionality is now available on Android, which is the preferred device type in the developing world. More will come in the following months, and Instagram tells me its exploring an iOS version. Instagram engineer Hendri says offline users will be able to see content previously loaded in Instagram’s feed. People can leave comments, Like things, save media, or unfollow people — all of which will go through when they reconnect. Profiles…
Read MoreApple planning an iPhone overhaul
Ten years after Steve Jobs held up the original iPhone to a gushing San Francisco crowd, Apple Inc. is planning its most extensive iPhone lineup to date. The tech giant is preparing three iPhones for launch as soon as this fall, including upgraded versions of the current two iPhone models and a new top-of-the-line handset with an overhauled look to commemorate its iPhone’s 10th anniversary in grand fashion, according to a new report. The technology giant is working on three iPhone models this year, including one that will deliver an…
Read MoreArtificial intelligence could be the key to cyber security
In a constantly evolving digital threat landscape, where firewalls and antiviruses are considered tools of antiquity, companies are looking to more technologically advanced means of protecting crucial data. Experts point out the cyber-threat landscape has drastically changed and that criminals are now using more artificial intelligence technologies to launch sophisticated attacks. Even a few years ago, launching a distributed denial of service attack to take down a website, defacing webpages and stealing credit card details were considered major instances of cyber-attacks. Today, anything from medical records to airline miles data…
Read More