Discontent on Continent Highlights Battle Over Economics, Culture, Internet Control BRUSSELS—From Berlin to Madrid, from London to Paris, U.S. technology companies are in a pitched battle with Europe’s sovereign states. It is a clash that pits governments against the new tech titans, established industries against upstart challengers, and freewheeling American business culture against a more regulated European framework. And it poses one of the greatest threats to U.S. technology giants since their emergence from garages and college campuses over the past four decades. First and foremost, the battle is about…
Read MoreCategory: TECH
The cyberattack on Sony Pictures made employees collateral damage
The wave of cyberattacks of large retailers, from Target to Home Depot, over the past year have made hacks feel like a fact of life for many consumers. But the alleged breach at Sony Pictures last week hints at a future where such attacks are more invasive than a stolen credit card: Documents allegedly leaked include Social Security numbers, salary information and even employee performance reviews. The leaked documents, first reported on by Kevin Roose at Fusion, have not yet been verified by Sony. But a memo sent to employees by Sony Pictures executives obtained by the…
Read MoreEuropean Regulators Publish Right To Be Forgotten Guidelines
Europe’s Article 29 Working Party, the body comprised of data protection representatives from individual Member States of the European Union, has now published guidelines on the implementation of the so-called right to be forgotten ruling, which was handed down by Europe’s top court back in May. The European Court of Justice Right To Be Forgotten ruling gives private individuals in Europe the right to request that search engines de-index specific URLs attached to search results for their name — if the information being associated with their name is inaccurate, outdated or irrelevant. The ruling…
Read MoreBlack Friday – consumers warned to be vigilant
On the eve of the much-anticipated retail focused sale and discount event, Black Friday, consumers in key regions across Africa, such as Kenya, are warned by network security experts to be vigilant. Black Friday and Cyber Monday are acknowledged as two of the busiest shopping days of the year, involving contribution by social networks and ecommerce websites. Global network security company Fortinet, and its research division FortiGuard Labs, are warning shoppers to be wary. The Company has issued important tips than can keep consumers safe, both when shopping online or…
Read MoreWashingtonPost: Why Obama’s plan to save the Internet could actually ruin it
On Monday, President Obama joined the chorus of those urging FCC Chairman Tom Wheeler to inject federal and state regulators directly into the heart of the Internet, “reclassifying” wired and mobile broadband ISPs as public utilities under a 1934 law written to control the former Bell telephone monopoly. While Obama has long supported the notoriously slippery idea of “net neutrality,” this is the first time the White House has explicitly asked the FCC to take specific action, let alone to embrace the most radical and legally uncertain approach being considered…
Read MoreFacebook secretly working on new website called ‘Facebook at Work’ for office use
London (AFP) – Facebook is preparing a new office version of its social networking site to compete with other sites like LinkedIn, the Financial Times reported on Monday. “Facebook is secretly working on a new website called ‘Facebook at Work’” that would allow users to “chat with colleagues, connect with professional contacts and collaborate over documents”, it said. Facebook last month reported its quarterly profit nearly doubled to $802 million (640 million euros) but saw its stock pounded after outlining a plan to invest heavily in the future instead of…
Read MoreApple downplays Masque bug risk for users of iOS devices
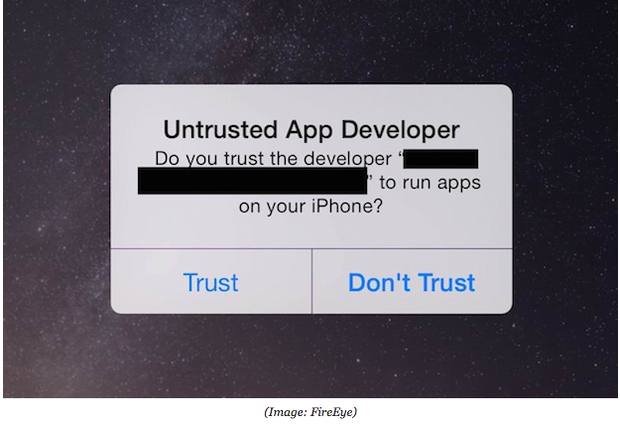
Apple has downplayed exploit fears stemming from the discovery of a security loophole which could trick users into downloading malicious apps on to their iOS devices. On Monday, security researchers at FireEye detailed the discovery of the Masque bug in a new report. The researchers said the bug, in which apps running on iOS 7.1.1 and later — including the latest iOS 8 — can be replaced with malicious, legitimate-looking applications. Once granted access to a user’s device, these apps could theoretically install malware or steal user data. The “Masque…
Read MoreApple users raise privacy concerns after hard-drive files uploaded to iCloud
Line between devices and cloud services fades as online storage allows users to switch without losing data by Craig Timberg for the Washington Post
After security researcher Jeffrey Paul upgraded the operating system on his MacBook Pro last week, he discovered that several of his personal files had found a new home – on the cloud. The computer had saved the files
The creators of Google Inbox explain why it’s the future of Gmail
Google’s on a mission to reinvent email. Its weapon: Inbox, a standalone app that launched last week. Inbox aims to make email more useful with several new tools. It surfaces relevant content (photos, for example) and information from within individual messages so you don’t have to open anything to get at what you really want. Bundles sort your messages for you, letting you find important messages faster. Plus you can add your own reminders that work with Google Now. But there’s something important that Inbox isn’t: Gmail. Although the whole…
Read MoreUnauthorized software is proliferating in the workplace, What apps are your employees using?
Unauthorized cloud-based software is proliferating in the workplace, causing regulatory and security challenges for companies that often don’t even know their employees are using it. Some of the services are well known, such as Dropbox, for file sharing, and the multipurpose social-media site Facebook . But at some companies, employees are tapping hundreds of cloud-based apps to perform functions ranging from Web conferencing to conducting surveys to sharing photos. Skyhigh Networks, a provider of services that track and control cloud apps, surveyed more than 350 large companies this year and…
Read More