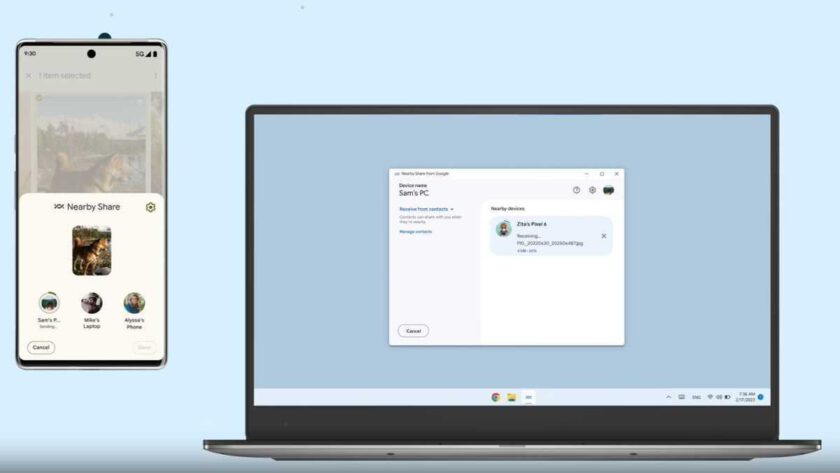
“Hey, it’s OurMine Team, we are just testing your security, please send us a message.”
Earlier this summer, that message was blasted out to my followers on Twitter… only I didn’t send it. I had been hacked.
It was embarrassing. I run Hootsuite, a social media management company that prides itself on world-class security for our customers. How could this happen? What did I do wrong?
In the following days, I learned that Ev Williams, the co-founder of Twitter, had fallen victim to the same hackers. And not long before that, Mark Zuckerberg’s Twitter and Pinterest accounts were compromised. So I wasn’t the only one who could have been more proactive on security.

Even so, it should never have happened. After doing a postmortem to see what went wrong in my case, I learned a few basic security lessons that will hopefully help other executives and professionals keep their own accounts safe from hacking.
Beware of the side door. My hack had nothing to do with Twitter or Hootsuite (which I use to manage my Twitter account) themselves being compromised. The hackers who breached my account actually gained entry through a completely different app that I hadn’t used in years. At some point, I had enabled Foursquare to access my Twitter account (this is known as “app authing”). Later, there were reports that Foursquare was hacked and some accounts were compromised. My IT team confirmed that hackers used that info to get into my Twitter.
Today, app authing is even more common. Most social platforms have multiple points of access through partner services—just think of how many apps, from Airbnb to WordPress, integrate into Facebook, for instance. So step one in safeguarding your social media is removing the apps no longer being used, generally via the network’s settings panel. In the case of Twitter, for example, you can see a list of all the services you’ve authorized in the apps tab of your settings page, then remove those that are no longer in use. Step two is being cognizant of which platforms have been breached recently or in the past. A handy resource is the site Have I been pwned, which will allow you to search across multiple data breaches to find out if your user information in particular has been compromised.
Change your passwords. People are tired of hearing this, but strong passwords—those with lots of random numbers and symbols—actually make a huge difference in keeping your accounts safe. If you can’t think of your own, services like LastPass, which generate and manage random passwords, can help. The hackers who gained access to Zuckerberg’s accounts evidently took advantage of his exceptionally weak password: “dadada.” Worse, he had used the exact same password for several different platforms and may not have changed it for years.
Sharing isn’t caring. Even a strong password won’t help if you share it around. Lots of CEOs (myself included) get help from staff with their social media. A natural inclination is just to share your log-in info, but a safer way of granting access is instead using social media security tools that let you authorize other users, without having to divulge your actual password. That way your credentials start and end with you, and you can pinpoint the source of any security breach. (A basic social media audit can reveal how far and wide your password has been spread.)
Two-factor is a no-brainer. After my hacking incident, I did something I should have done a long time ago: I enabled two-factor authentication on my Twitter account. You’ve probably been prompted to do this on several platforms…and ignored the option. But it’s worth the tiny extra headache. Instead of just entering a password, you’ll be asked to enter a special code sent to your phone when logging in from a new location or device. It takes an extra few seconds, but it makes it harder to hack your account.
Careful where you click. We all know by now not to respond to those emails from Nigerian princes. But newer phishing scams, where people attempt to trick you into divulging sensitive information by posing as a reputable company or individual, can be hard to detect and easy to fall victim to. Phishing is up 150% this year on social media, so avoid clicking on links from unfamiliar or suspicious users. Fake customer service accounts are a common ploy, as are accounts designed to look like friends or followers. Basic rule of thumb: don’t divulge user names and passwords unless you’re absolutely sure of the authenticity of the site. This, sadly, happens all the time, especially when communications appear to come from a bank, credit card company, or other service you actually use and trust.
Have someone (or something) at the helm. My hackers struck late on a Saturday night, which was likely no accident. They were hoping that it would be hours before I spotted the fake Tweet, or enough time for my followers to click on it. For executives, who can’t always be monitoring their social feeds, having the right plan in place for these kind of occurrences is critical. For starters, be sure someone is monitoring your feed. After hours, this can be supplemented with monitoring tools that sense unexpected spikes in activity or register a rise in negative mentions. It’s also critical to have a “chain-of-command” chart spelling out who can intervene on your behalf if you’re unavailable, as well as a set of pre-approved responses. Doing a “crisis drill” in advance is a great way to ensure that you have the proper protocol to detect and respond to a breach.
When you’re hacked, time is of the essence. Getting hacked is bad enough. But getting hacked and not responding swiftly makes the situation exponentially worse. For starters, your colleagues and followers are out there clicking on bogus updates from you, compromising the trust you’ve built with them. Plus, hackers will only be emboldened by your indifference to take more aggressive steps. In my case, we were able to immediately delete the offending Tweet, as a first critical step, and I also changed my Twitter password. In this instance, however, hackers were accessing my account through an entirely different service. By revoking access to third-party apps, I was able to stop the breach. Then I changed the passwords on those outside apps, as well, denying the hackers their point of entry and getting to the root of the problem. All of this happened within a few minutes, so what could have been a disaster was instead an important wake up call.
Ultimately, no account or server is entirely hack-proof, as recent high-profile breaches of the Democratic National Committee and World Anti-Doping Agency have shown. But some common-sense steps can go a long way toward safeguarding executives on social media. After all, social media is where your customers, colleagues and employees are. Sitting on the sidelines really isn’t an option. They key is to dive in, with the right protections in place.
Adapted from HBR