China is using fake LinkedIn profiles to gather information on German officials and politicians, the German intelligence agency (BfV) has said. The agency alleges that Chinese intelligence used the networking site to target at least 10,000 Germans, possibly to recruit them as informants. It released a number of fake profiles allegedly used for this purpose. BfV head Hans-Georg Maassen said the accounts show China’s efforts to subvert top-level German politics. “This is a broad-based attempt to infiltrate in particular parliaments, ministries and government agencies,” he said. China has denied similar…
Read MoreCategory: Cybersecurity
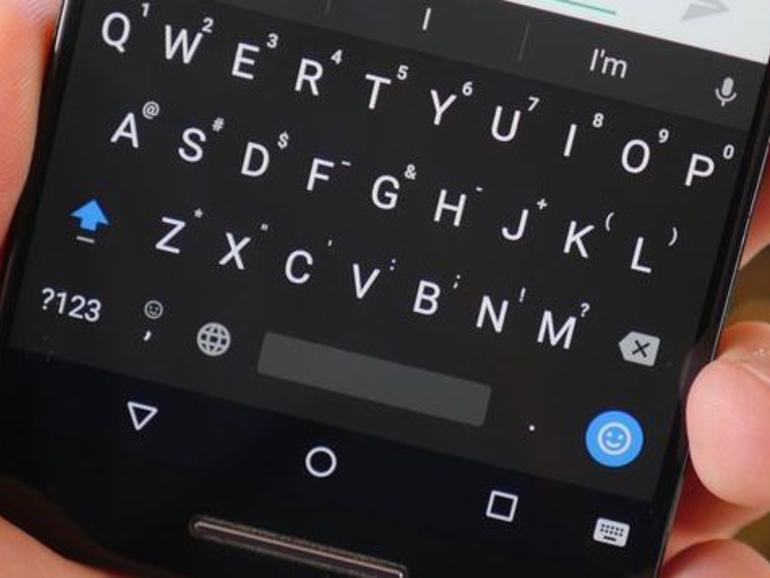
Millions caught in virtual keyboard app data breach
Security researchers claim to have found the personal data of 31 million Android users of the keyboard app Ai.type after finding an open database online. The app offers themed keyboards for phones and tablets.The researchers claimed data left visible included names, phone numbers, locations and Google queries. The boss of the Israeli company behind the app admitted the breach but said most of the data was not sensitive. Bob Diachenko, from the Kromtech Security Centre, part of security company Mackeeper, said the amount of data required by the app at…
Read MoreSEC’s new cyber unit takes its first action to halt an initial coin offering ‘scam by PlexCorp
The Securities and Exchange Commission has charged Canadian crypto company PlexCorp with violating securities laws by selling up to $15 million in an initial coin offering (ICO). ICOs have seen explosive growth over the past year as fledgling companies have used them to raise more than $3 billion in capital through various cryptocurrencies. However, experts have warned they can present several dangers to unsuspecting investors hoping to get into a hot new market as regulations are pretty loose. Called PlexCoins, PlexCorp allegedly used this cryptocurrency to scam would-be investors hoping…
Read MoreThe UK’s cybersecurity agency issued a new guidance to ministries about using Russian antivirus software
The UK’s National Cyber Security Centre (NCSC) has issued a new guidance for how the country’s various ministries should closely manage their use of antivirus software supplied by a foreign nation, such as Russia’s Kaspersky Lab. In a letter to to heads of government ministries, NCSC CEO, Ciaran Martin said that organizations need to be vigilant to the risk that an [antivirus] product under the control of a hostile actor could extract sensitive data from that network, or indeed cause damage to the network itself. He went on to specifically…
Read MoreGoogle faces mass legal action in UK over data snooping
Google is being taken to court, accused of collecting the personal data of millions of users, in the first mass legal action of its kind in the UK. It focuses on allegations that Google unlawfully harvested information from 5.4 million UK users by bypassing privacy settings on their iPhones. The group taking action – Google You Owe Us – is led by ex-Which director Richard Lloyd. He estimates the users could get as much as “several hundred pounds each”. The case centres on how Google used cookies – small pieces…
Read MoreUber Paid Hackers to Delete Stolen Data on 57 Million People
Hackers stole the personal data of 57 million customers and drivers from Uber Technologies Inc., a massive breach that the company concealed for more than a year. This week, the ride-hailing firm ousted its chief security officer and one of his deputies for their roles in keeping the hack under wraps, which included a $100,000 payment to the attackers. Compromised data from the October 2016 attack included names, email addresses and phone numbers of 50 million Uber riders around the world, the company told Bloomberg on Tuesday. The personal information…
Read MorePhishing Makes It Easy To Hijack Accounts
Cyber-thieves grab almost 250,000 valid log-in names and passwords for Google accounts every week, suggests research. The study by Google and UC Berkeley looked at the ways email and other accounts get hijacked. It used 12 months of log-in and account data found on websites and criminal forums or which had been harvested by hacking tools. Google said the research helped secure accounts by showing how people fell victim to scammers and hackers. During the 12 months studying the underground markets, the researchers identified more than 788,000 credentials stolen via…
Read MoreCovert influence, the new money laundering
Google is the most recent company known to have discovered evidence of Russian covert influence on its books. As more media companies realize Russia bought advertising space or promoted news stories, fake and otherwise, on their platforms, covert influence has become the new money laundering. Both activities hide below the surface of legitimate enterprises, cast a shadow of disrepute on those very enterprises and can be neutralized through transparency and accountability. Anti-money laundering laws provide useful lessons for combating covert influence and could be adapted for online media models that do…
Read MoreGambling companies warned against using images appealing to children
Britain’s betting industry faces its biggest crackdown on child gambling after regulators demanded that operators pull hundreds of casino games, that contain graphics and images that are likely to be attractive to minors, from their websites. Regulators said the “unacceptable” ads and third-party media, should be “immediately” removed or amended adding that this particularly applied to adverts for free and pay-to-play games. In a joint letter, the regulators said under-18s and other vulnerable people should be protected from exploitation. The Gambling Commission, the Advertising Standards Authority, the Committee of Advertising…
Read MoreNew Bluetooth vulnerability can hack a phone in 10 seconds
More than 5 billion devices are vulnerable to a “highly infectious” malware attack. Go ahead, blame the internet of things. More than 5.3 billion devices with Bluetooth signals are at risk of a malware attack newly identified by an internet of things security company. If you’re not keeping count, that’s most of the estimated 8.2 billion devices that use Bluetooth, which allows for our gadgets to connect and communicate in wireless. Nearly every connected device out there has Bluetooth capability. Your phones, laptops, speakers, car entertainment systems — the list goes…
Read More