Kaspersky researchers detected a Trojan application that terrorizes users with unsolicited ads and boosts installations of online shopping applications. This malicious app visits smartphone app stores, downloads and launches applications and leaves fake reviews on behalf of the user, all while hiding itself from the device owner. As sales are hitting the stores, both users and brands need to be wary. When choosing shops, users rely heavily on reviews, while retailers increase their promotion and advertising budgets. As it turns out, neither can fully trust what they see online, as…
Search Results for: Malicious
Spyware attacks on organizations in South Africa, Kenya and Nigeria increased in Q1 2023
South Africa, Kenya, and Nigeria reported an increase in spyware attacks in Q1 2023 according to Kaspersky. Thin clients are used in corporate networks around the world to set up workspaces at a much lower cost than when using traditional laptop or desktop computers (thick clients). A thin client on a traditional operating system (OS), Linux or Windows-based, could potentially be targeted by different types of attacks, including spyware. A compromised thin client could serve as an entry point to the corporate network, and it could be used to gain…
Researchers Devise iPhone Malware that Runs even when Device is turned off
Researchers Devise iPhone Malware that Runs even when Device is turned off Research is largely theoretical but exposes an overlooked security issue When you turn off an iPhone, it doesn’t fully power down. Chips inside the device continue to run in a low-power mode that makes it possible to locate lost or stolen devices using the Find My feature or use credit cards and car keys after the battery dies. Now researchers have devised a way to abuse this always-on mechanism to run malware that remains active even when an…
Russia is exploring options for cyberattacks
Russia is exploring options for cyberattacks President Joe Biden on Monday advised U.S. corporations to strengthen their cybersattacks. practices because of intelligence reports indicating that Russia is looking at potential attacks. The guidance came almost a month after Russian troops invaded Ukraine in a war that has killed more than 900 people, including 39 children. “I have previously warned about the potential that Russia could conduct malicious cyber activity against the United States, including as a response to the unprecedented economic costs we’ve imposed on Russia alongside our allies and…
Microsoft Office 365 subscription Scam
Microsoft Office 365 subscription Scam Phishing campaigns work by impersonating some well-known organization or brand, and that certainly includes a company like Microsoft. With products like Windows, Office, Outlook, and OneDrive prevalent among consumers and businesses, Microsoft is a tempting target for cybercriminals to spoof. Two recent phishing attacks analyzed by security provider Abnormal Security use a subscription renewal as the pitch to trap unsuspecting users. Abnormal Security described in a Friday blog post, two separate phishing campaigns, both of which impersonate actual notices from Microsoft. The goal is to…
Kaspersky partners with Arctic Security
Kaspersky has announced a new partnership with Arctic Security. Through this collaboration, Kaspersky Threat Data Feeds will be available out-of-the-box, on Arctic Security’s Arctic Hub platform. These feeds will help organisations with Security Operation Centers, as well as managed security service and internet service providers, to obtain the most up-to-date and relevant information about cyberthreats. Not all information about cyberthreats is helpful. For instance, 37% of information security executives say that there’s too much security data to deal with and not very much of it is actionable – as revealed by…
Samsung partners with Safaricom and M-kopa
Technology firm Samsung has partnered with Safaricom and M-Kopa to roll out a Pay-As-You-Go mobile phone solution in Kenya. This initiative is described as a world first mobile security solution enabling carriers, financial partners and retailers running installment plans to remotely manage Samsung devices. The initiative will leverage the benefits of Safaricom’s fast 4G data network and service in Kenya. Essentially, the pay-as-you-go initiative will enable carriers and dealers to expand their current customer base with lower upfront fees and interest rates. It offers customers the opportunity to access a…
Researchers have found a vulnerability in two popular email encryption protocols
European security researchers have found an alarming new vulnerability in the most common forms of email encryption. The attack, described in a report published Monday morning, lets bad actors inject malicious code into intercepted emails, despite encryption protocols designed to protect against code injection. Implemented correctly, the malicious code could be used to steal the entire contents of a target’s inbox. The vulnerability affects two of the most common email encryption protocols, PGP and S/MIME, although the degree of vulnerability depends heavily on the client’s implementation of the protocol. A…
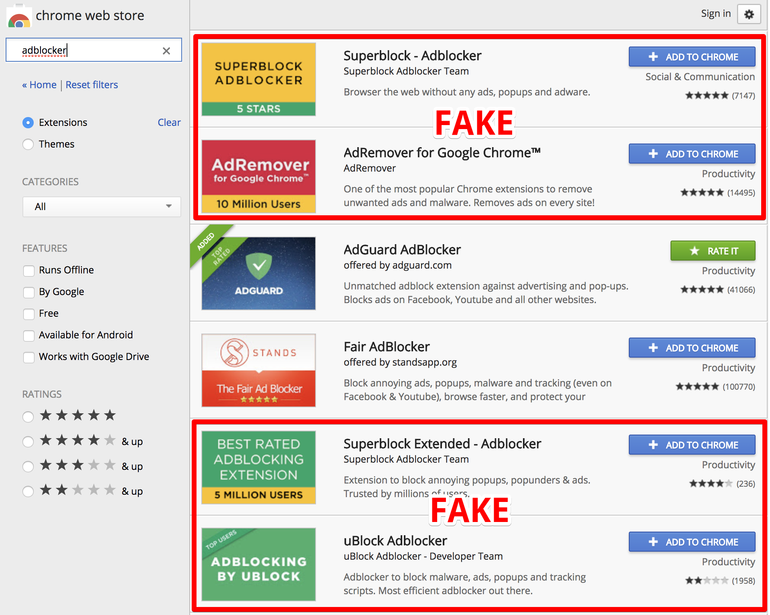
Google Gets Rid of Fake Chrome Ad Blockers
Research unearths five malicious ad-blocker extensions on the Chrome Web Store that were installed by 20 million Chrome users before Google removed them. The bogus ad blockers were discovered by researchers at AdGuard, a Moscow-based maker of ad-blocking and anti-tracking tech. Following AdGuard’s report on the fake ad blockers in the Chrome Web Store, Google removed the suspect extensions, which have been installed on 20 million Chrome instances over the past year. The most popular fake ad blocker was AdRemover for Google Chrome, which had over 10 million users, putting…
No More Bulk Tweeting and Duplicate Accounts on Twitter
Twitter is announcing major limits on how users and apps can automate tweets, in order to curb spam and political propaganda bots. Developers are now banned from using any system that simultaneously posts “identical or substantially similar” tweets from multiple accounts at once, or makes actions like liking, retweeting, and following across multiple accounts at once. Twitter will remove these options from its own TweetDeck app, and third-party developers have until March 23rd to comply. Twitter says these actions are “an important step in ensuring we stay ahead of malicious…